Product Center
Leading Performances
Accurate identification
Identification ability of an Internet behavior management product is the key factor to decide whether it is effective. The management will only be effective when the product has wide identification range and high identification accuracy.
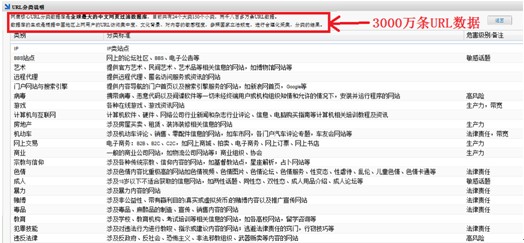
 Leading webpage identification ability
Leading webpage identification ability
With the world's largest Chinese web page classification library built-in, the product can identify contents on 30 million websites.
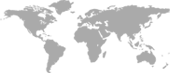
 Leading applications identification ability
Leading applications identification ability
With over 1500 main trend net application protocols built-in, the product is totally independent of IP and ports. No matter how IP and ports change, even under circumstances of encryption, the product can always identify applications.
 Leading update frequency
Leading update frequency
Web classification library is updated every day and application protocol library is updated every two weeks, effectively preventing failure of identification caused by the changes of websites and applications.
Humanistic management:
Internet behavior management products can effectively avoid employee’s conflict. Interment management system can only be actually executed with abundant, flexible and humanistic management modes.
 Rich management elements
Rich management elements
Policies can be set flexibly based on people, time, location and application types.
 Employee self-management
Employee self-management
The product enables employees to reasonably arrange Internet behavior by humanistic ways like time limit and flow limit instead of simple rough blocks which may bring conflict.
Safe and reliable
Internet behavior management products are usually connected in series in network and can audit a lot of sensitive information, so high reliability and data security protection is needed.
 Double system boot
Double system boot
- When one system does not work, another system will take the place.
 Intelligent hardware bypass
Intelligent hardware bypass
- The product will automatically trigger direct connection state in cases of system crash or power off to avoid network break.
 NetentSec light path bypass
NetentSec light path bypass
- This product supports fast connection at equipment exceptions in optic fiber lines, avoiding network break.
 Data transmission anti-eavesdrop
Data transmission anti-eavesdrop
- All equipment management and data access are completed with encryption, ensuring that the data transmitted in network will not be eavesdropped.
 Separation of powers
Separation of powers
-
The power of network administrators, logauditors and permission checkers are separated, ensuring that the network administrators cannot see sensitive information.
-
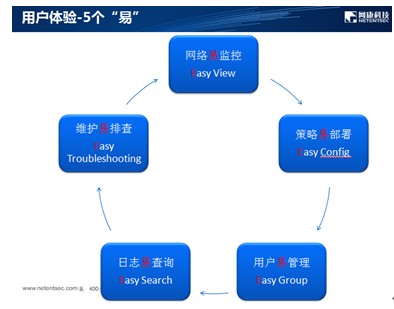
Simple and easy to use
Internet behavior management products need be able to quickly follow up the development of network behavior, and the configuration and upgrade need be simple.
 Simple interface
Simple interface
- All operations are graphically designed.
 Simple update
Simple update
- All database updates are one-click operation.
 Simple upgrade
Simple upgrade
- The administrator can do one-key upgrade when a new version is available.